Synergistic Financial Networks Pvt Ltd
CR100
Acceptable Use Security Policy
1
Purpose
This document objective is to describe the Security Policy for usage of the CR100 from Synergistic Financial Networks Pvt Lrd. The document was made to provide information to operator (Merchant) about product overview, guidance and administration as per PCI Requirements.
Using any unapproved usage that is not addressed in this document and its references will violate the PCI PTS approval of the device. You shall be responsible for all risk arises out of usage which are not authorized and described in this document and agree to not to hold SFN liable.
2
General Description
2.1
Product Name and Appearance
The product name is CR100. It is visible on the label of device (on the back of device), and should not be modified by any way, or covered by any sticker.
2.2 Product Type
CR100 is a Secure Card Reader PIN (SCRP) handheld device for payment processing in an attended environment.
It provides the ability to conduct contact and contactless transactions. When used in conjunction with a Commercial off-the-shelf (COTS) device, the mobile host device and CR100 together acts as a payment processing terminal at the point-of- interaction. The operation flow is partially controlled by the mobile host device and partially by the CR100. The PCI approval is only valid when using the device as described in this document. Use of the device in an unapproved method will violate the PCI PTS approval of the device.
The device contains the following physical and logical interfaces:
• USB interface
• ICC reader
• Contactless reader
• Bluetooth module
2.3
Identification
The operator agrees to use only below approved CR 100 as listed in PCI PTS.
Firmware Version – 1.1.1, Hardware Model Version – CR100
Details can be verified over PCI PTS site here
https://www.pcisecuritystandards.org/assessors_and_solutions/pin_transaction_devices
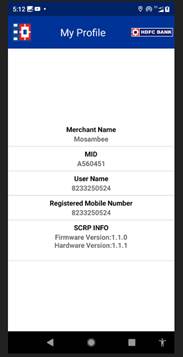
The Operator shall verify the same against received device as shown in figure 3 via PIN CVM APP. Each device has a unique serial number that is used to keep track of devices during lifetime from production to decommission. The unique serial number can be also obtained by system commands to double check the authenticity of the label. Further operator agrees to use the PIN CVM APP on Android 10 and above devices as comply with accepted systems basslines.
The full view of the device is presented in Figure 1.
|
|
Figure 1 - CR100 full view
There is an identification label located on the back cover of the device, which contains the model, HW, S/N, etc., as shown Figure 2. This label must not be torn off, covered or altered.

Figure 2 - Product identification label
All product information, especially the serial number, should be checked after receiving the product to guarantee that the item received is authentic.
CR100 has mainly two versions:
• Hardware version: 1.1.0
This version can be visually checked on the back of the device at the product identification label (see Figure 2)
• Firmware version: 1.1.1
The connected device version can be checked through “about” section of PIN CVM Application.
Figure 3 – Connected device identification
2.4
SCRP Specification
SCRP model CR 100 and Firmware Version 1.1.1 is PCI PTS certified. This model uses DES3 DUKPT, AES encryption algorithm which are verified under PCI PTS certification. This device is approved for use with PIN's and to provide PIN translation.
Details can be verified over PCI PTS site here
https://www.pcisecuritystandards.org/assessors_and_solutions/pin_transaction_devices
3
Installation and User Guidance
3.1
Initial inspection
After receiving the product, the items listed below must be inspected:
The product identification, that includes the product version and the serial number on the back label;
• The serial number on the back label is the same as the one recorded in the product system, that should be displayed on the PIN CVM Application;
• The warranty label, whether is present and not damaged;
• The ICC acceptor, for shim or any obstruction or suspicious objects;
• The appearance of the entire device for any tamper evidences, including cuts, holes, cracks, wires, additional stickers, glue marks and any other suspicious elements;
• The application behavior and all logical information, such as versions, date and others control numbers available to confirm that any unauthorized changes were made.
If any item is not completely normal, the device should be sent immediately to maintenance. The CR100, as any of secure equipment from DSPREAD TECHNOLOGY (Beijing) INC, passes for security procedures when sent back for maintenance. These procedures aim to keep the security of the devices.
3.2
Installation
Prior starting to use the terminal, it is recommended to check the user manual available for download in the product.
3.3 Environment Conditions
The following are the temperature and humidity specifications of the device:
• Operating temperature: 0° to 50° C (32° to 122° F)
• Storage temperature: -20°C to 70°C (-4° to 158° F) Relative humidity: 5% to 95% (RH non-condensing)
Subjecting the device to extreme environmental conditions will result in tamper events.
Any temperatures above 109ºC (± 5º) or below -39ºC (±5º) will result in a tamper condition. Additionally, if the backup battery voltage drifts outside of the range of 1.90 VDC to 3.62 VDC, the unit will tamper as well
3.4 Communications and
Security Protocols
The CR100 supports USB and Bluetooth 4.2 BLE without configuration.
The „Just Works‟ is used in Bluetooth communication and the mutual authentication and channel encryption must be used for data transmission. And these functions are provided by the firmware.
3.5 Configuration Settings
After released to the market, the device does not have any security sensitive configuration set-up necessary to meet security requirements
4
Operation and Maintenance
4.1
Periodic Inspection
For security reasons, it is strongly recommended the daily inspection of the items listed in section 3.1 of this document.
4.2 Self-Test
A complete self-test that check all integrity and authenticity of the device is performed upon start and the device will reboot in 24 hours after it starts up.
The self-test is performed automatically, so no initialization by an operator is required. Once any failure is detected in this process, the buzzer will ring until the problem is solved and any operation will be blocked.
4.3
Roles and Responsibilities
The device has no functionality that gives access to security sensitive services, based on roles. Such services are only available in authorized facilities managed through dedicated tools, using cryptographic authentication. Below table shows different roles and operations:
Table 1 Different roles and operations
|
|
Role |
Operation |
|
Service Provider |
administrator |
Develop PIN CVM application to connect the SCRP and backend monitoring, attestation system |
|
Merchant |
operator |
Hosting solutions developed by Service Provider |
|
Dspread |
maintainer |
Repair device and unlock the device if tampered |
|
End User |
user |
Perform transactions |
4.4
Passwords and Certificates
After released to the market, the device does not have any security sensitive configuration set-up necessary to meet security requirements.
4.5 Tamper Response
The device has a protection mechanism for physical tamper attack. At the tamper event, the device rings the buzzer three times every second and will block any operation. Also, the connected PIN CVM application will display the tampered state to inform the user that the device cannot be used.
If the device is in tampered state, the user must contact the device maintenance or authorized center immediately, remove it from service and keep it away from potential illegal investigation.
4.6 Patching and Updating
The firmware can be updatable remotely. The service provider has all rights to communicate with service provider to perform device patching or update remotely. The user shall support and provision the availability of device for remote patching.The opeartor shall be responsible for any risk associated with not updating device firmware within 40 days of patch update being available and notified. It is recommended to use the latest stable version of firmware.
4.7
Decommissioning
When the device is no longer used for permanent decommissioning reason, the operator of the device needs to notify the service provide to initiate the decommissioning process of device
4.8
Privacy for PIN Acceptance
The operator must ensure privacy while accepting pin on PIN CVM Application through following ways
· Handing over COTS device to end user ensuring within range of 2 meters from scrp device.
· Ensuring no presence of shoulder surfing
· Highlight the message to end user “securely enter a pin”
· Encouraging end user to exercise all precaution while entering a pin to avoid being recorded or seen by others.
4.9
Storage
The operator must keep the device in secured location with lock and key post usage of device.
4.10
Do & Don’ts
The operator/merchant must follow below Do’s and Don’ts ensure PCI compliance.
Do’s
· Understand the flow of customer data in your payment system
· Encourage end user to enter pin securely
· Use dedicated device for PIN CVM Application,
· Update PIN CVM Application whenever update is available
· Regularly update android device for security patches, os updates
· Call mosambee support center for device, Application related queries
Don’ts
· Store cardholder information
· Store authentication data including the CVV or CVC code on the card
· print cardholder data
· Store cardholder data on unprotected devices like computers, laptops, or smartphones
· Send cardholder data through texts or email messages
· Place payment card system storage devices anywhere but not in a secure and access-controlled room
· Participate in data security activity that doesn’t follow PCI regulations
· Try to open or repair device on your own or with third party
· Not to inform service provider for device damage or loss
· Using rooted android device, Installing screen capture and / or keypad strokes application in the android device.
5
Operators / Merchants Responsibility
Operator shall be responsible for providing and maintaining the means by which operator access the Application, which may include, but is not limited to, your mobile device, Mosambee device, and telecommunication service provider.
Operator shall be responsible for all access and service fees necessary to connect to the Application and assume all charges incurred by use of such connectivity services. Operator further assume all risks associated with the use and storage of information on your device or device through which operator will gain access to the Mosambee Application and the Services (hereinafter referred to as "Device").
Operator represent and warrant that operator have implemented and plan to operate and maintain appropriate protection in relation to the security and control of your Device and any information and data included therein.
Operator agree that SFN will not be liable in any way to operator in the event of failure of or damage or destruction to operator Device systems, data or records or any part thereof, or for delays, losses, errors or omissions resulting from the failure or mismanagement of any telecommunications services or Device equipment or software.
Operator will not in any way, whether directly or indirectly, expose SFN or any of SFN's service providers to any Device virus or other similarly harmful or inappropriate material or device.
SFN reserve the right to disconnect the merchant / operator if any vulnerabilities and or actions found on cots devices used that could result exposure of PIN DATA.
SFN reserves the right to suspend the operation of this operator for failure to maintain any part or sections of this document for CR100 at any time and no claims may be entertained against the Company in connection thereto.
